NSA Stole Millions Of SIM Card Encryption Keys To Gather Private Data
:)
Edward Snowden is back with one of the biggest revelations about the government's widespread surveillance program.
The US National Security Agency (NSA) and British counterpart Government Communications Headquarters (GCHQ) hacked into the networks of the world's biggest SIM card manufacturer, according to top-secret documents given to The Intercept by former NSA-contractor-turned-whistle blower, Edward Snowden.
OPERATION DAPINO GAMMA
The leaked documents suggests that in a joint operation, the NSA and the GCHQ formed the Mobile Handset Exploitation Team (MHET) in April 2010, and as the name suggests, the unit was built to target vulnerabilities in cellphone.
Under an operation dubbed DAPINO GAMMA, the unit hacked into a Digital security company Gemalto, the largest SIM card manufacturer in the world, and stole SIM Card Encryption Keys that are used to protect the privacy of cellphone communications.
Gemalto, a huge company that operates in 85 countries, creates about 2 Billion SIM cards each year for AT&T, T-Mobile, Verizon, Sprint and about 450 manufacturers worldwide. The SIM card manufacturer giant also produces banking cards, electronic passports, identification cards and other digital security solutions.
HOW DID SPIES HACKED INTO GEMALTO ?
As The Intercept describes, it was a real caper. MHET targeted individual employees in major telecom corporations and SIM card manufacturer companies by accessing their email and Facebook accounts using theNSA's XKeyscore.
XKeyscore surveillance program was designed by the NSA to collect and analyse intercepted data it finds traveling over a network. XKeyscore is powerful enough to be able to pull up more than 20 terabytes of information daily, including emails, chats, social media interactions, and even browsing histories all in real-time, as The Hacker News reported in 2013.
"In effect, GCHQ clandestinely cyber stalked Gemalto employees," the report reads, digging up all information they could find that would lead them back to Gemalto's systems and made it possible to steal large quantities of SIM Card Encryption Keys.
In one case, the report claims, the GCHQ operatives suspiciously targeted a Gemalto employee in Thailand because he was using PGP to encrypt data, who they think "would certainly be a good place to start" for their operation.
The document also noted that some of the companies involved in SIM production didn't take strong measures to protect users’ personal and sensitive data. According to report, "many" SIM card manufacturers sent the encryption keys to wireless network providers with weak encryption methods that can be broken or no encryption at all.
HOW SPY AGENCIES MONITOR YOU MOBILE COMMUNICATION ?
All mobile communications are private because of the encrypted connection between an individual's mobile and the wireless carrier's network. The encryption keys to decrypt that communication is in every phone's SIM card.
These keys basically allow mobile communications – both voice and data – to be decrypted without alerting the users, networks or governments of any activity.
Once stolen, the SIM Card Encryption Keys grants the US and British agents the ability to secretly monitor "a large portion of the world’s cellular communications," both voice calls and data, from 450 wireless network providers without the approval of telecom companies or foreign governments.
HOLY SHIT! MY VOICE AND DATA ARE MONITORED ?
This may have given the spying agencies power to silently and effortlessly eavesdrop on anyone’s communications done over a cellphone without leaving any tell-tale trace.
NSA and its counterpart GCHQ could intercept and decrypt any communications, anytime and anywhere they want. This could make it a lot easier for the agencies to conduct widespread surveillance of wireless communications without getting warrants or asking permission from telecom companies or foreign governments.
HELL OF A HEIST
The breach is devastating for mobile security, which has been targeted a numerous of times. According to the Intercept, it’s hell of a heist. "Gaining access to a database of keys is pretty much game over for cellular encryption," said cryptography specialist Matthew Green.
NSA’s attempt to break into a major corporation and steal private encryption keys that protect hundreds of millions of users worldwide isn't surprising behavior. Because, past two years revelations about the NSA and its allies taught us that they can go to any extent in order to collect data and break or interfere with security on the Internet.
At the beginning of the month, Snowden revealed about the NSA and GCHQ efforts to track and monitor the activities of independent and state-sponsored hackers, some security researchers and news agencies, including The Hacker News, in order to pilfer the stolen data from hackers' archives and to gather information on their targets respectively.
Apart of this, the latest revelation is really a bad news for pretty much everyone around the world having cellphones in their pockets, since it's highly likely that your mobile phone contains a Gemalto-manufactured SIM card, and which means your conversations can be easily monitored.
The revelation is also a bad news for countries, except the U.S. and U.K., since these SIM Card Encryption Keys give them an easy way to spy on foreign countries without asking permission. And last but not the least, it’s really bad news for the biggest SIM card manufacturer Gemalto, as the agencies cyber stalked and hacked its employees to obtain the private encryption keys.
03:25
Android Malware Can Spy On You Even When Your Mobile Is Off
:)
Security researchers have unearthed a new Android Trojan that tricks victims into believing they have switched their device off while it continues "spying" on the users' activities in the background. So, next time be very sure while you turn off your Android smartphones.
The new Android malware threat, dubbed PowerOffHijack, has been spotted and analyzed by the researchers at the security firm AVG. PowerOffHijack because the nasty malware has a very unique feature - it hijacks the shutdown process of user’s mobile phone.
MALWARE WORKS AFTER SWITCHING OFF MOBILES
When users presses the power button on their device, a fake dialog box is shown. The malware mimics the shutdown animation and the device appears to be off, but actually remains on, giving the malicious program freedom to move around on the device and steal data.
"After pressing the power button, you will see the real shutdown animation, and the phone appears off. Although the screen is black, it is still on," AVG’s mobile malware research team explained in a blog post. "While the phone is in this state, the malware can make outgoing calls, take pictures and perform many other tasks without notifying the user."
HOW DOES POWEROFFHIJACK MALWARE WORKS ?
Once installed, the malware asks for root-level permissions and tampers with the 'system_server' file of the operating system to affect the shutdown process. The malware particularly hijacks themWindowManagerFuncs interface, so that it can display a fake shutdown dialog box and animation every time the victim presses the power button.
The nasty malware is apparently being propagated via third-party online app stores, but the researchers haven't mentioned the names of the the innocent-looking apps, also they haven’t explained how the malware gains the root access of the device. The code shown by AVG appears to contact Chinese services.
USERS AND ANDROID VERSIONS INFECTED
According to the company, PowerOffHijack malware infects devices running Android versions below 5.0 (Lollipop) and requires root access to perform the tasks.
So far, PowerOffHijack malware has already infected more than 10,000 devices, mostly in China where the malware was first introduced and offered through the local, official app stores.
PowerOffHijack malware has ability to silently send lots of premium-rate text messages, make calls to expensive overseas numbers, take photos and perform many other tasks even if the phone is supposedly switched off.
EASY STEPS TO GET RID OF POWEROFFHIJACK
In order to get rid of PowerOffHijack malware, users are advised to take some simple steps:
In order to get rid of PowerOffHijack malware, users are advised to take some simple steps:
- To restart infected device manually just take out the battery.
- Remove malicious, untrusted and useless apps from your Android device.
- Do not install apps from 3rd Party app stores.
- Make sure you have a good anti-virus installed and updated on your mobile devices. AVG antivirus product can detect PowerOffHijack malware.
03:08
‘DarkLeaks’ Black Market — Anonymously Selling Secrets for Bitcoins
:)
An all new anonymous online underground black market website, DarkLeaks, has been introduced on the Internet where Whistleblowers, blackmailers, hackers and any individual can trade/sell sensitive and valuable data/secrets anonymously in exchange for Bitcoin payments.
DarkLeaks is a decentralized underground blackmarket which is built on top of the Bitcoin Blockchain technology and is available on the Internet to download as a free software package together with its source code published openly on code-sharing site Github.
TRADE INFORMATION ANONYMOUSLY
DarkLeaks underground black market website is masterminded by the members of crypto-anarchist collective System. "There is no identity, no central operator and no interaction between leaker and buyers," the developers'statement says.
"DarkLeaks is a decentralized black market where you can sell information," according to the blog post about the new site. "It has a mechanism for trust-less authentication of documents that are being sold through a novel cryptographic mechanism. The authentication is fair, provably fair."
Blockchain technology is developed for secure Bitcoin payments, where users can make transactions directly without need of any intermediary. Blockchain encrypts the files which are released when payment is claimed by the leaker.
NO LIMITS TO TRADE CONTENTS
The developers of DarkLeaks underground black market website said that it is the best tool to trade any kind of secret, illegal or confidential, but valuable data, including media, information, video, data and documents. The list of contents that can be shared is as follows:
- Hollywood movies
- Trade secrets
- Government secrets
- Proprietary source code
- Industrial designs like medicine or defence
- Zero day exploits
- Stolen databases
- Proof of tax evasion
- Military intelligence
- Celebrity sex pictures
- Corruption
HOW DOES DARKLEAKS WORK ?
The files on sale are encrypted by DarkLeaks black market website, broken into smaller pieces, and then added to Bitcoin's block chain. However, the service allows the buyer to verify small preview piece of the file before payment is claimed.
After buyer purchase the rest of the file when satisfied with the contents, the seller claims their Bitcoins. A decryption key is provided to the buyer in order to unlocks the encrypted document for the buyer. "The mechanism involved makes the environment free from intervention."
DON'T BE AFRAID, JOIN HANDS WITH US
The concept is different, but isn't new, as many existing portals, such as the infamous WikiLeaks, used for sharing secret information by whistleblowers and others, but has never been an opportunity to exchange those information for profit.
However, DarkLeaks is taking things to the next level, making the information sharing portal a direct purchase transaction.
The developers say that Darkleaks will help "stop corruption and challenge power", and at the same time encourage users by saying, "Don't be afraid. Come join the revolution and reclaim your freedom. The gloves are off. The revolt has begun."
If you want to share your opinions about DarkLeaks, Feel free to comment below.
03:07
Google releases Cloud-based Web App Vulnerability Scanner and Assessment Tool
:)
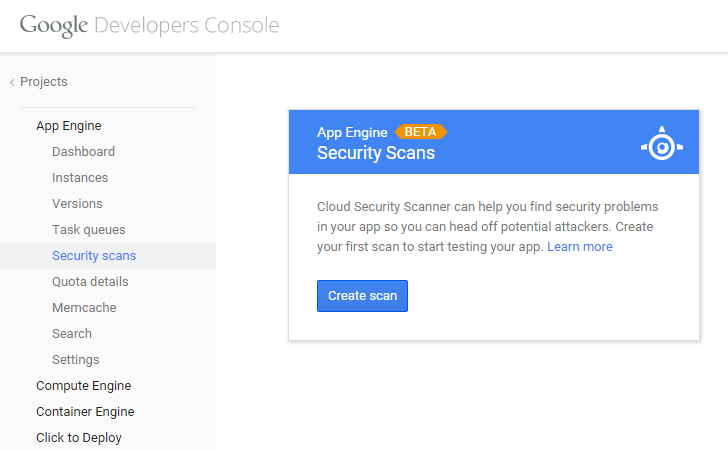
Google on Thursday unleashed its own free web application vulnerability scanner tool, which the search engine giant calls Google Cloud Security Scanner, that will potentially scan developers' applications for common security vulnerabilities on its cloud platform more effectively.
SCANNER ADDRESSES TWO MAJOR WEB VULNERABILITIES
Google launched the Google Cloud Security Scanner in beta. The New web application vulnerability scanner allows App Engine developers to regularly scan their applications for two common web application vulnerabilities:
Google launched the Google Cloud Security Scanner in beta. The New web application vulnerability scanner allows App Engine developers to regularly scan their applications for two common web application vulnerabilities:
- Cross-Site Scripting (XSS)
- Mixed Content Scripts
Despite several free web application vulnerability scanner and vulnerability assessment tools are available in the market, Google says these website vulnerability scanners are typically hard to set up and "built for security professionals," not for web application developers that run the apps on the Google App Engine.
While Google Cloud Security Scanner will be easier for web application developers to use. This web application vulnerability scanner easily scans for Cross-Site Scripting (XSS) and mixed content scripts flaws, which the company argues are the most common security vulnerabilities Google App Engine developers face.
Today, common HTML5 and JavaScript-heavy applications are more challenging to crawl and test, and Google Cloud Security Scanner claims to take a novel approach by parsing the code and then executing a full-page render to find more complex areas of a developer's site.
GO FOR WEB VULNERABILITY SCAN NOW
The developers can access the Cloud Security Scanner under Compute > App Engine > Security in Google's Developers Console. This will run your first scan. It does not work with App Engine Managed VMs, Google Compute Engine, or other resources.
Google notes that there are two typical approaches to such security scans:
- Parse the HTML and emulate a browser – This is fast; however, it comes at the cost of missing site actions that require a full DOM or complex JavaScript operations.
- Use a real browser – This approach avoids the parser coverage gap and most closely simulates the site experience. However, it can be slow due to event firing, dynamic execution, and time needed for the DOM to settle.
Security Engineering head Rob Mann says that their web vulnerability scanner uses Google Compute Engine to dynamically create a botnet of hundreds of virtual Chrome workers that scan at a max rate of 20 requests per second, so that the target sites won’t be overloaded.
"Cloud Security Scanner addresses the weaknesses of [real and emulated browsers] by using a multi-stage pipeline," Mann wrote in a blog post. "As with all dynamic vulnerability scanners, a clean scan does not necessarily mean you're security bug free."
The search engine giant still recommended developers to look into manual security review by a web app security professional, just to be on the safer side. However, the company hopes its vulnerability scanner tool will definitely provide a simple solution to the most common App Engine issues with minimal false positives.
03:05
Subscribe to:
Posts
(
Atom
)